How To Set Up A Trusted SD Card For Saving Private Bitcoin-Related Files Across Ubuntu 16.04 Temporary Live-Boot Sessions
Introduction
There is a pair of conflicting requirements when performing bitcoin-related tasks. On one hand, it is a complicated thing with lots of hard-to-type hexidecimal-encoded and base58-encoded information that must be exact. On the other hand, this is private information that we would rather not leave lying around for someone to find in the future, so you would rather not create excessive digital copies.
Here, we will show you how to properly set up an encrypted SD card for saving files. This allows you the convenience of being able to save documents while keeping the security standard high.
This guide assumes you previously set up a temporary Ubuntu 16.04-based live boot session by following the article:
Should You Use a USB Flash Storage Drive Instead?
SD cards have some security advantages over USB flash storage devices. First, USB devices are more complicated and a modified (ie. hacked) USB drive can do more malicious things than a modified SD card. A USB drive can present to your PC more than just a connected storage device that can possibly exploit your OS at a root level. Second, it is physically easier to hide something malicious in it. To suggest an example of something malicious that is possible, the plastic enclosure of the USB drive could hide a microphone and a wireless interface that gets powered when you plug it in and the audio patter of your keystroke presses, not to mention the words you speak could be broadcast to someone else nearby.
If you have a Laptop or PC with a built-in SD card reader, the security advantage is that they are only capable of powering an SD card and can only present to the OS a storage device. If it is a micro-SD card, it is significantly harder to hide something nasty in the plastic enclosure. If you have a PC that has a SD card reader that actually just connected via USB to the motherboard internally, the security advantage is diminished since that reader is accessible and open to the same set of exploits as a USB drive. Most laptops with a card reader will have a more native SD card reader that does have the security advantages.
All things being equal, it is better to use a SD card. If, due to your circumstances, you wish to use a USB drive instead, we have a similar article tailored for that on Ubuntu.
Buying A SD Card For Secure Use With Bitcoin
It is advisable that you do not re-use a spare SD card for this use that that has been lying around. To be sure it has not been tampered with physically or has picked up malware ahead of this use. It is best you buy it brand new from a physical brick-and-mortar store. In that, you get to show up at a random time and pick one randomly from a store rack ahead of you setting it up. Since we are dealing with Bitcoin and perserving anomynity is desirable, it is advisable to purchase this SD card using cash. This will prevent some future record linkage between the serial number of this SD card and your fiat banking information.
The good news is that the best recommendation is to buy the absolute cheapest SD card available at the store. The cheaper it is, the less remorse you will have when it comes time to 'securely erase'. Also, fancy features, drive speed and capacity is generally not a concern for this use.
Set Up Encrypytion
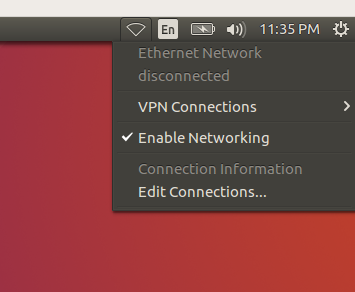
Since the goal is to maximize security, there is no need for a network connection while working on the SD card. If your PC has some means of disabling the WiFi via an external switch or disconnecting the Ethernet connection by unplugging the cable, it is best if you boot the temporary session up without the connection. This will ensure that this OS instance has been completely isolated from the Internet for its entire duration. You can verify this by checking the connection status in the upper right menu:
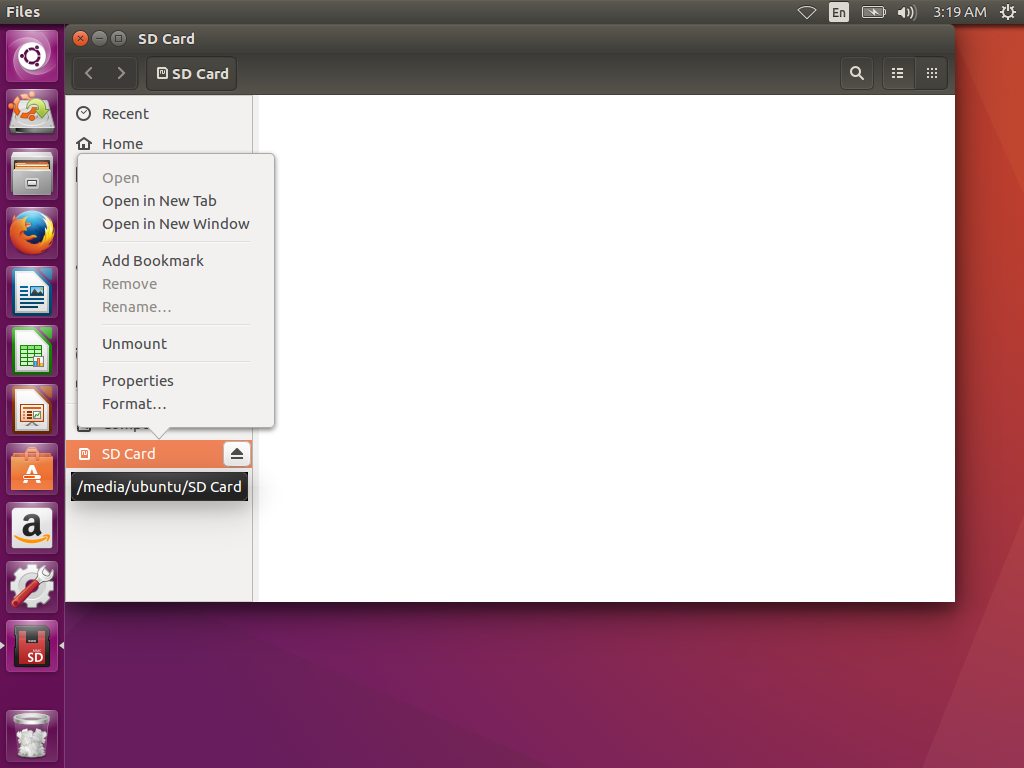
When you insert the card into your card reader, it should pop up a File Manager window with the drive automatically mounted for your use. It will appear in the side menu of the window near the bottom. In order to reformat the drive and set up encryption,
we need to right-click on it and select the Format... option:
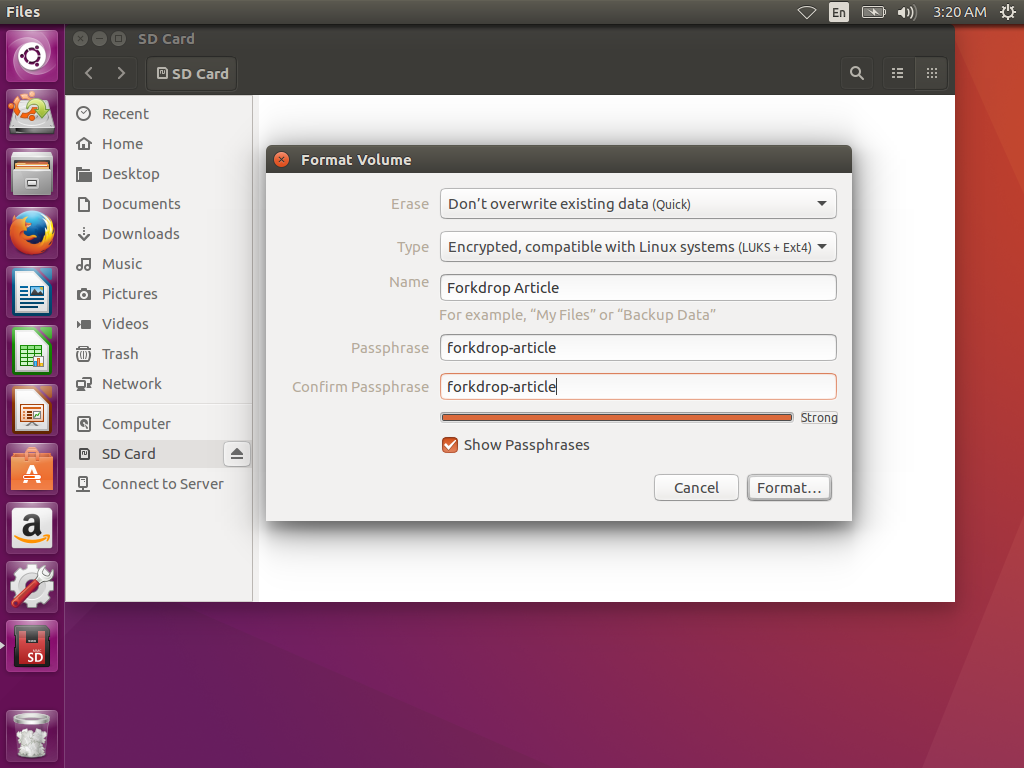
In the dialog that appears, we want to select the options Don't overwrite existing data (Quick) and Encrypted, compatible with Linux systems, (LUKS + Ext4). We want to give the drive a name Forkdrop Article here, and a relatively secure passphrase:
It will prompt you before it proceeds to format the volume. Stop and make sure that this is indeed the drive you intend and not some other drive connected to your system that was selected by mistake. Pressing the Format button will permanently overwrite the contents of this drive:
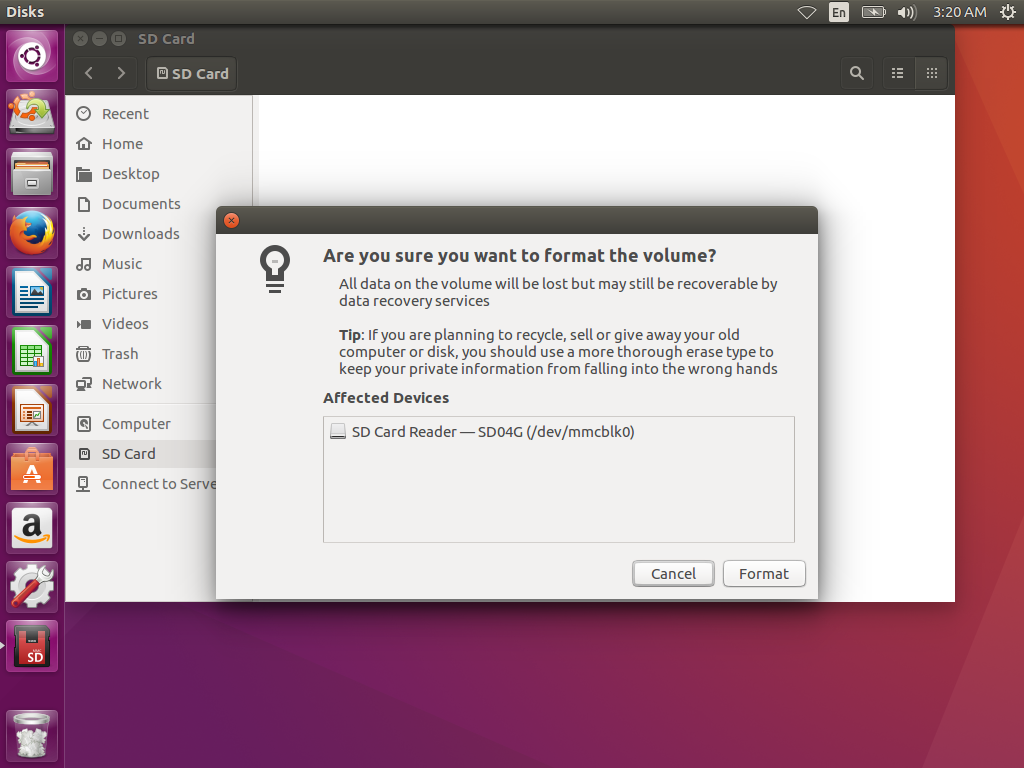
Ubuntu doesn't give you a progress report. It may look like nothing happened, and you might see some devices flicker in and out from the File Manager window. It should take a minute or two to fully finish. When it does, your named device will re-appear in the side menu of the window like so:
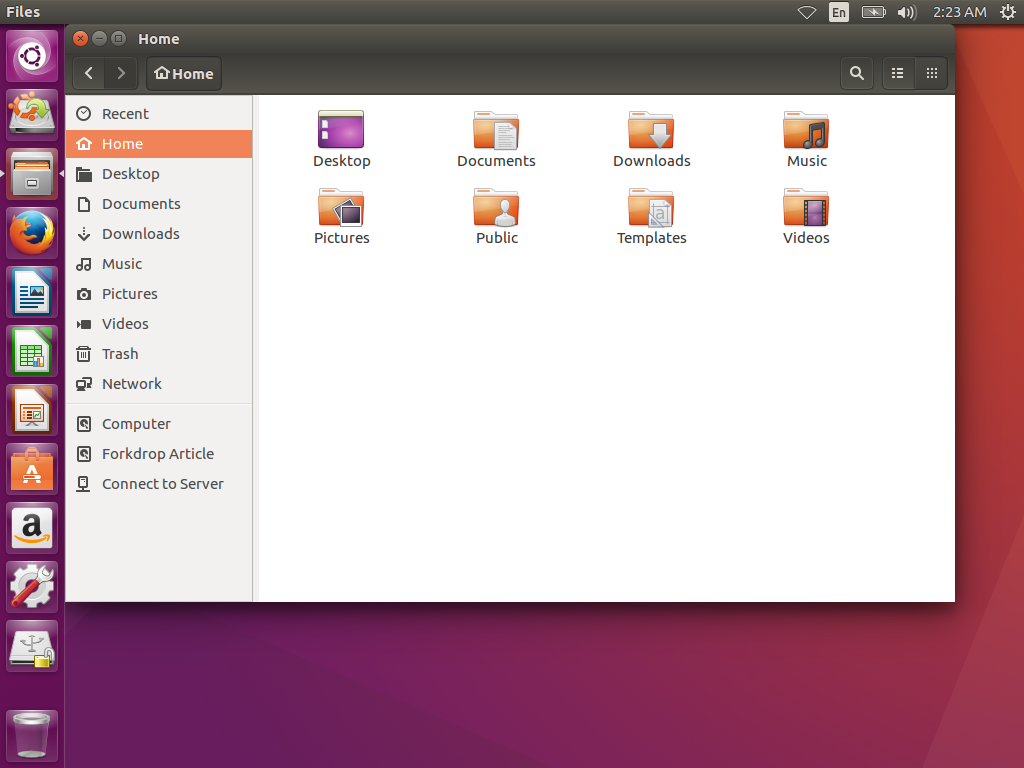
If it doesn't appear, make sure you have waited 10 minutes or longer before trying to disconnect the SD card. This could be a case of it being a particularly slow drive.
If you haven't unplugged the device, you should be able to mount it without the password by clicking on it. However, we want to make sure the device can be mounted by providing the password. If you click on the device to mount it, and then press the Eject icon to unmount it, you can then unplug the SD card. You can then close all windows to a blank desktop. When you plug it back in, you should get a password prompt:
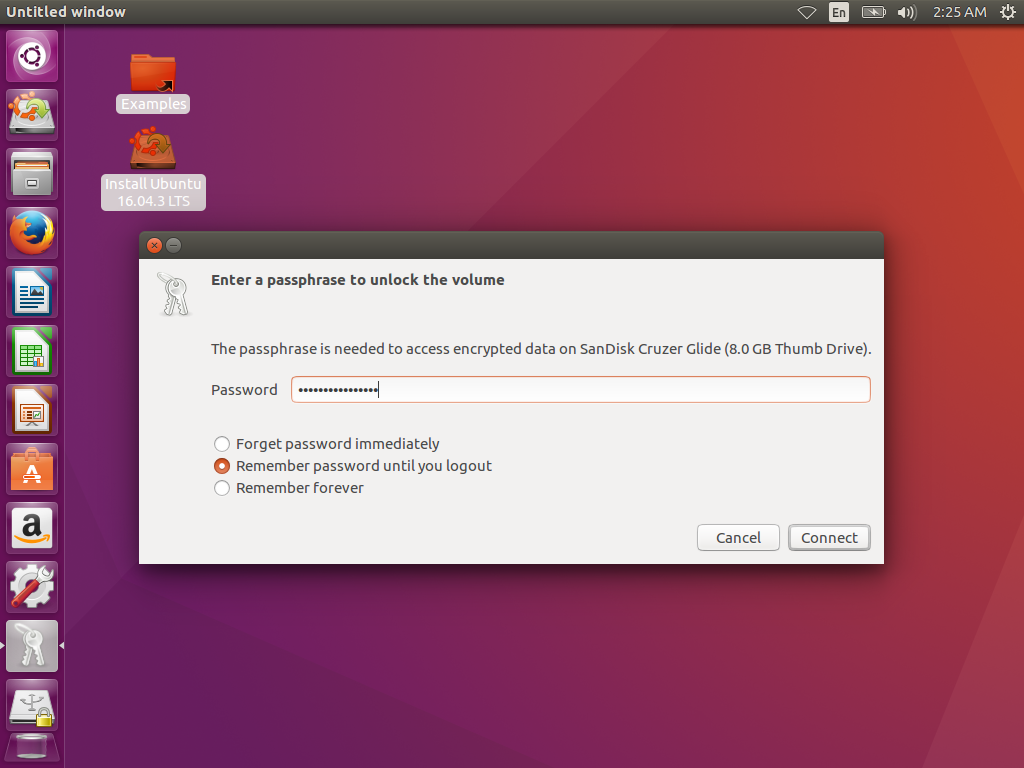
If it accepts your password, it should show you a blank mounted SD card:
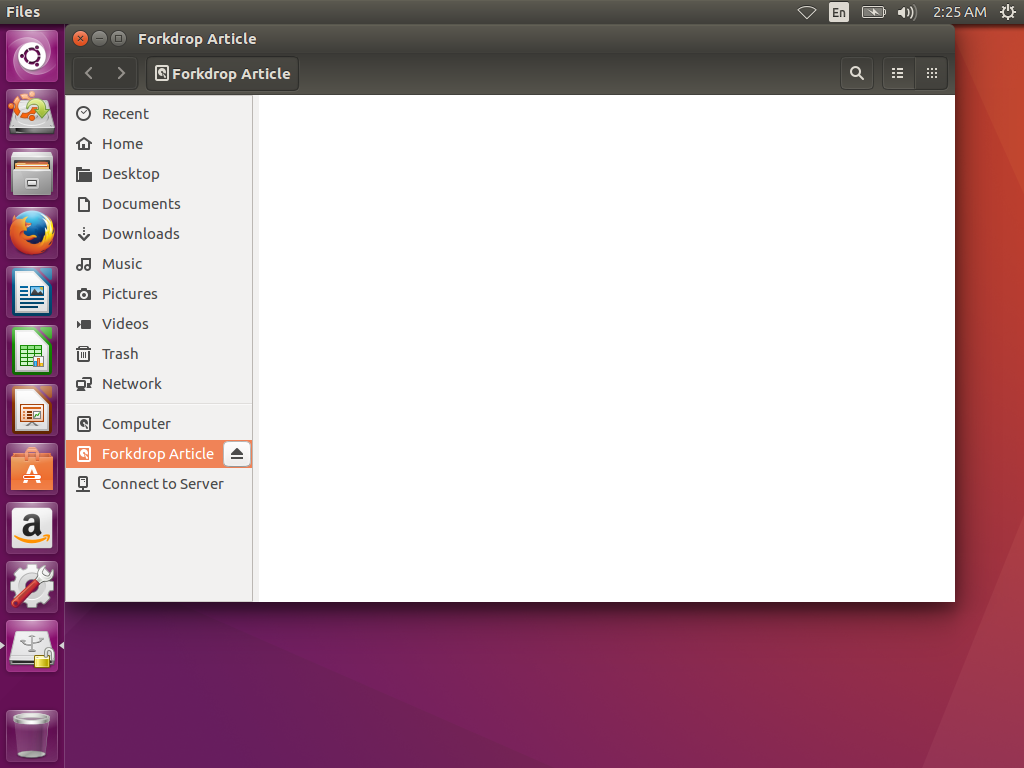
What To Do With This Card Afterwards
If you wish to keep the SD card and the written data afterwards, do be sure to store it in a safe, physically-protected location. If you are worried about the password being found or guessed, do consider destroying the drive beyond repair. Also, be aware that if the data is not set up to be encrypted, permanently erasing all of the data beyond recovery is quite difficult, so there is no good advice that can be offered other than complete destruction.
