Choosing An Electrum Server For Using Forkdrop Suite

The Problem
Blockchain.info provides a Tor hidden service to access their block explorer. They also provide a full-feature API for writing applications such as fork-coin finders. The information we need to find forked coins is the ability to look up the historical transaction record for any given address.
On the surface, using a block explorer via Tor is great however there are a couple issues that come with it. First, this is a centralized service that requires some level of trust that they will not record and attempt to correlate your queries with your other web presences. Second, this .onion gateway has reliability issues which make applications written against it unavailable when the API is unavailable. Providing and maintaining an .onion gateway requires some specialized skills and if there is no profit incentive for blockchain.info, this is a charitable act. Hence, this kind of solution can not be relied upon indefinitely.
The Solution
The ideal in Bitcoin is to write decentralized applications, and the Electrum projectis one such application. It is a SPV wallet that can operate as a thin client without the blockchain, but it relies on Electrum server hosts to stay online and provide relevant updates from the Bitcoin (BTC) network. These servers are designed to operate in a decentralized, independent fashion just like Bitcoin (BTC) nodes.
TheElectrum Server Protocol provides the interface for querying information from an Electrum server. For any given Bitcoin (BTC) address, it can provide the history of transactions as well as unspent balances.
Unlike with a block explorer, the transaction data comes back in a raw format that is not presentable for easy human readability. To parse this transaction data, Forkdrop Suite utilizes python-bitcoinlib which is a multi-purpose framework of Python code for inter-operating with the Bitcoin (BTC) network.
Using these two services, Forkdrop Suite can avoid using a centralized block explorer to find fork coins on a given set of addresses. However, this requires you take the additional step of selecting an Electrum server to query from.
Finding an Electrum Server
Part of the point of decentralization is that it is up to you to find an Electrum server and discriminate for quality. Doing some google searches allow you to locate servers that operate on the web and also some with .onion addresses. By default, Electrum server's access port for SSL connections is 50002, however some servers choose to configure that differently. For .onion servers operating as hidden services, SSL is not necessary and port 50001 is the usual choice. In practice, some of these advertised are no longer operational. Also, some of them return error codes to some commands unexpectedly. Therefore, it might take a bit of trial-and-error to find one that works for your uses.
It is also advisable to to run Forkdrop Suite against two or more selected servers to ensure that the information they are returning is the same and more likely to be accurate. Any discrepancy could be the result of a misconfigured our malicious node.
Using an Electrum Server
For the purposes of example, we will use the electrum server advertised at electrum-server.ninja, however, this is not an endorsement of this server or it's operator. We don't know anything about them other than they have a nice, straightforward and illustrative website for what we need.
If we are running from a non-TAILS system (and give the --not-tails option to force the script to proceed), to use this server, we can simply give the parameter --electrum-server electrum-server.ninja to claim-prep.py like so:
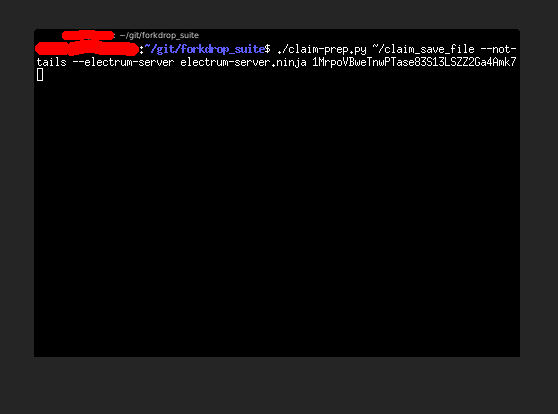
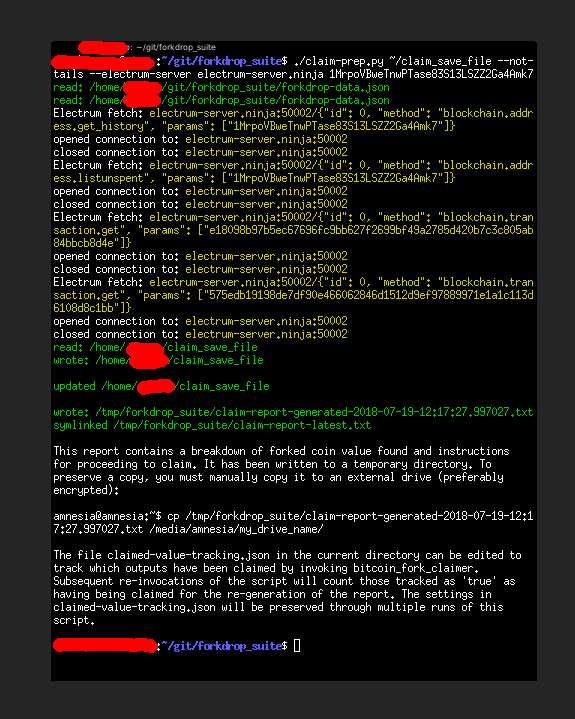
Running the command will show the connections in yellow to notify that this is not the most ideal connection (without the protection of Tor). It defaults to using SSL and port 50002:
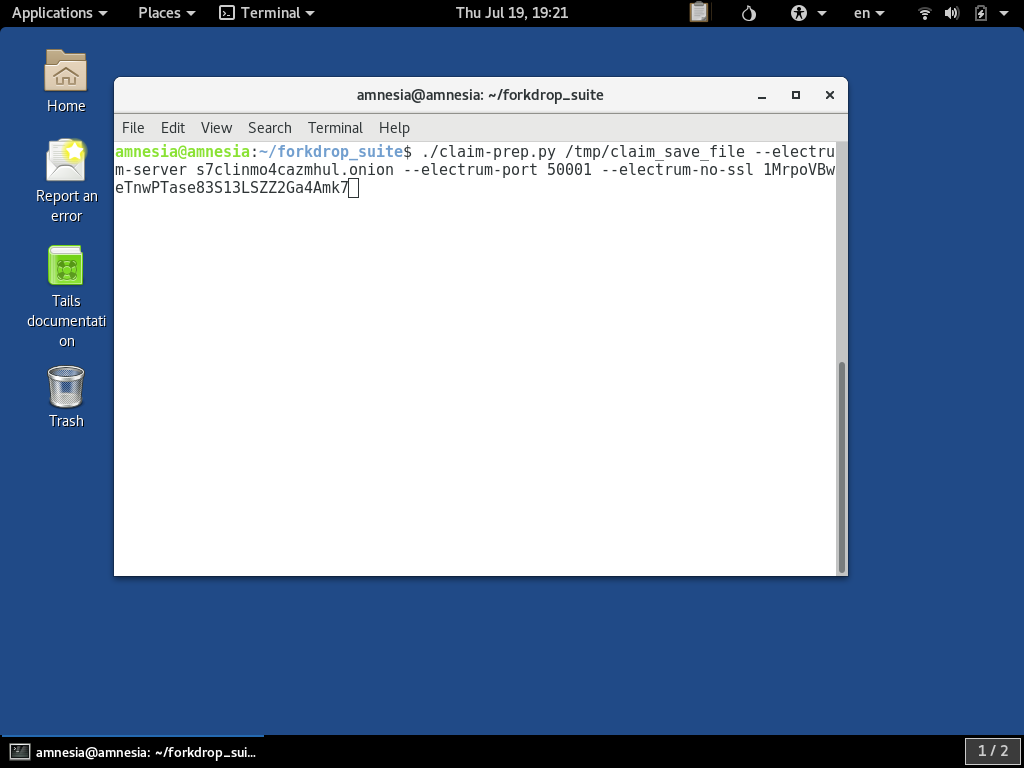
To use the server via Tor requires you give the .onion url instead. Also, you must specify the port 50001 and for it to not use SSL. No SSL is desired because the concept is redundant and invalid under Tor since the .onion address is the equivalent of an SSL certificate and the communication channel is already heavily encrypted and protected from interception. You must specify the parameters --electrum-server s7clinmo4cazmhul.onion --electrum-port 50001 --electrum-no-ssl like so:
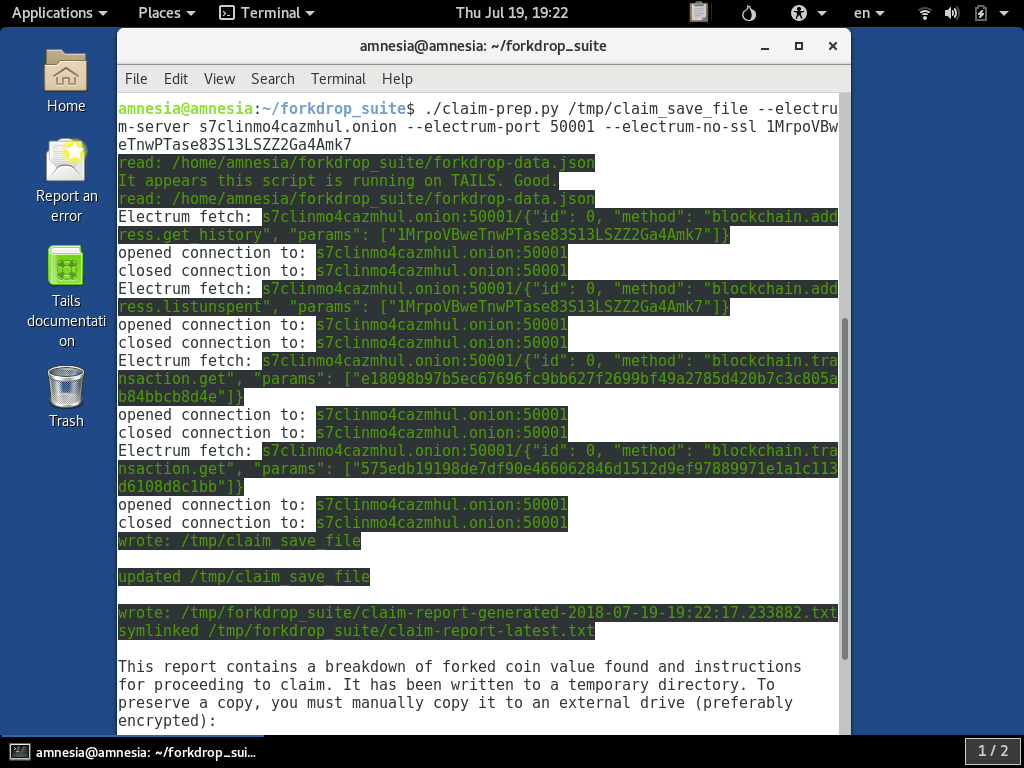
Running the command will show the connections in green to notify you that it is making a native Tor connection to the service like so:
Hosting your own Electrum Server
It is worth mentioning that for a more thorough 'trust no one' solution, hosting your own Electrum server will let you ensure that nobody malicious is operating it. There are many guides available that can help you with this. To access through Tor, you will need to connect the API port to Tor by also following one of many guides available
It is also conceivable that Forkdrop Suite be adapted to talk directly to a Bitcoin (BTC) Core full node instead of an Electrum server. However that requires the node to be set to 'watch' your set of addresses and have the RPC interface set up for you to be able to access it from your platform (such as TAILS, which requires a Tor link). If this is the type of feature direction you would like to Forkdrop Suite to take, please contact us and let us know.